Vishal Bhawnani, the Practice Head for Cyber Security Assurance at ProVise Secure Lab, speaks to Channel Post about the regional threat landscape

How do you expect the threat landscape to evolve in 2018?
These predictions are based on the research and development efforts by ProVise Secure Lab along with the threat observations across all our clientele in 2017. Apart from the below listed predictions, 2018 will also witness an increase in ransomware and IOT based attacks.
- Using the Actors and Attacks vector – We foresee 2018 will see lot more cyber-attacks and technology advancement in the Unknown Attacks and Unknown Attack vector
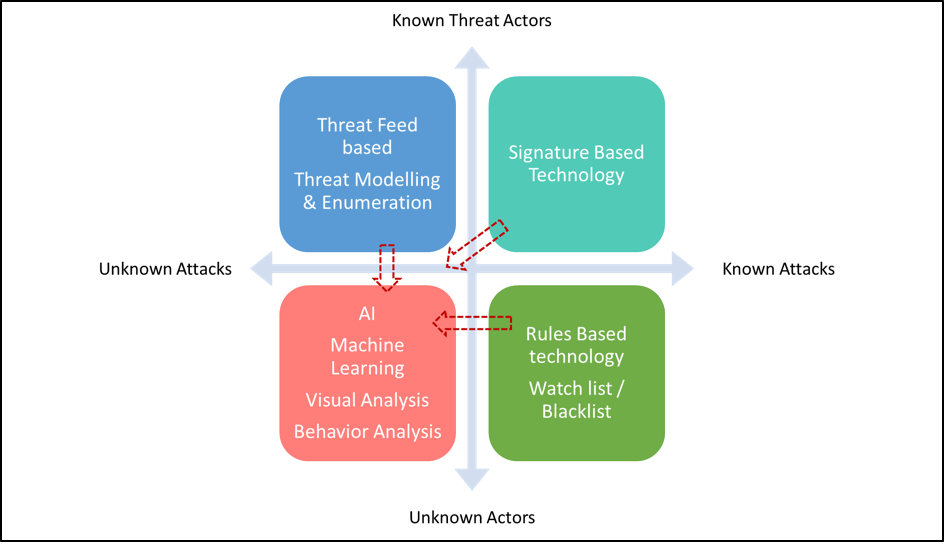
- Increase in state sponsored attacks– We see an increase in the use of Dark Web and evolution of cyber breach / crime as a service, as well as the use of intelligence profiling to measure the information spread over world wide web
- Third Party Integrations – There has been a rise in use of third party APIs, integration platforms and open APIs to establish an immix for communication across the application layer. Due to which exposure towards threats related to API’s and integrations have increased significantly and will continue to be considered as a critical risk in 2018 posing a severe threat to mission critical systems exposed over internet
- Wider acceptance of cloud based setup – Over the last two years, a majority of organizations have moved their infrastructure to cost effective cloud containers/setup to leverage the favourable features of computation, ease of management and deployment. This trend shall also be on rise in the year 2018, and will experience more cyber security breaches related to cloud infrastructure setup
- Increase in privacy related regulatory compliances– In 2018 and subsequent years there will be a stronger drive from various regions on stronger data privacy regulations, for instance GDPR.
Which technology trends are expected to impact the cyber security space and why?
- Transition from Threat Detection to Threat Deception– For the unknown attack and unknown vectors segment the technology advancement will move from detection to intelligent deception techniques
- Transition from DevOps to DevSecOps – 2018 will see more organizations adopting DevSecOps process and tightly bind development, security and operations across all phases within software development life cycle. This space will also see move from preventive controls to detective controls across all the phases
- Constructive and Destructive use of AI and ML Technologies – 2017 saw the inception of AI and ML in cyber security space, in 2018 organizations will effectively start using the intelligence from advanced analytics. The AI based approach can also be expected to help in identifying newer vulnerabilities that cloud be a potential exploit. Attackers would also use AI and ML to improve attack schemes by effectively collecting and analysing data forms on specific targets
How has the threat landscape changed over the past few years?
As per the pictorial representation in ‘Picture 1: Evloving Threat Landscape’, it can be visualized and observed that threat landscape is evolving to the quadrant of unknown attacks and unknown actors.
However, today’s evolving threats are more sophisticated, synchronized and unpredictable in nature and behaviour when it comes to attack pattern/attack signature based detection. Thereby the technologies based on classic intrusion detection and intrusion prevention mechanism will no longer be required within IT infrastructure.
What sort of industry verticals are largely at stake due to increased cyber security threats?
Due to increased cyber security threats and regional threats, the Banking and Financial Services vertical is always the lucrative target for attackers, especially for financial gains. However, every industry is venerable such as Oil and Gas, Telecom, Retail, and Government entities.
What according to you do companies need to do to keep themselves abreast of the latest security threats to mitigate damages?
Conducting information awareness within organizations will not be sufficient, and organizations should explore and effectively use technologies which are related to threat deception, MI, AL and visual analytics.
Tell us about the upcoming GDPR compliance in the UAE
On 25th May 2018, GDPR will come into effect across EU member states and outside EU. I believe that complying to GDPR will significantly enhance the overall security posture of organizations. With the target date approaching, most organizations are yet to complete implementation.
In the UAE, the general awareness about GDPR and applicability of GDPR saw a rise in Mid 2017, however the acceptance and implementation trends has rather been slow. This year will see organizations in UAE gearing up to this EU law, however implementation will be slow.
How is your company prepared to handle such GDPR compliance requirements for your clients?
ProVise has a phased approach to work with organizations that need to comply with GDPR. This approach helps identify readiness, assess the impact, discovery of data, protection impact analysis and implementation plan, identification of roles and institutionalization of practices to ensure ongoing compliance.
How can possible security threats from new tech such as IoT and cloud be handled effectively?
The threat landscape has seen a change in the last year and will continue to evolve and intensify this year too. Unfortunately, there is no silver bullet to address the best approach to handle these threats. The effective methods will also evolve for the newer technologies; we have witnessed the change from development operations to a secure development operation based on the changes in the development circles.
Similarly, the ground security rules (Hardening, Role based access, effective Patch Management etc) for all the organizations will remain the same and the further enhancements will be a continuous process. Organizations will also have to significantly invest time in building skillsets that specialize in this field apart from exploring the technology solutions that work on deception and not merely detection.












